Blog
Using an HMAC to Secure Endpoints
How secure are your API endpoints and webhooks? If you're not sure, read on to learn about HMAC security.

How secure are your API endpoints and webhooks? If you're not sure, read on to learn about HMAC security.


June 15th, 2022
How secure are your API endpoints and webhooks? If you're not sure, read on to learn about HMAC security.
In today's digital economy, data is constantly bouncing between various API endpoints. Everything in commerce, business and gaming communicates by sending relevant data to external systems. This data could contain private information like credit card details, social security numbers or other less important digital files like cat memes or emojis 😊. With all this information floating around in the cloud, some of it needs to be secured to ensure private communication.
Endpoint security has become a top priority in recent years for organizations of all sizes. One of the most popular ways to protect endpoints is by using HMAC. Let's review how this is done.
HMAC means "Hash-based Message Authentication Code" and is a type of code used to authenticate a message. HMAC is a cryptographic hash function that calculates a message authentication code (MAC) using a secret key. The MAC is a 128-bit value that is appended to the payload. The receiver can then use the same key to verify the MAC to ensure the message has not been tampered with.
HMAC is used in a variety of applications, including Transport Layer Security (TLS) and Secure Shell (SSH). It's also used to protect authentication credentials and cookies.
Here are some tips for protecting endpoints with HMAC:
Use a strong key. The key should be at least 128 bits in length.
Rotate the key regularly. The key should be rotated every few months.
Use a different key for each application.
Use a different key for each user.
Store the key in a secure location.
Use an HMAC algorithm that's resistant to attack.
Although HMAC is a powerful tool for protecting endpoints, there are some scenarios where it should not be used. For example, HMAC should not be used to protect data that's going to be stored in a public database.
When you submit a request to a web application, you often need to include some sort of authentication token to validate that the request is actually coming from you or your app. One popular way to do this is to use a cryptographic hashing algorithm, such as HMAC, to create a unique signature for the request. This signature can then be used to validate the request.
We'll show you how to use HMAC to generate a signature for a request, and then how to use that signature to validate the request. We'll be using a Node.js hash function to create the HMAC signature.
First, we need to set up a basic Node.js script that will generate the HMAC signature for a request. This script will need two parameters: the payload of the request, and the secret key that will be used to create the HMAC signature.
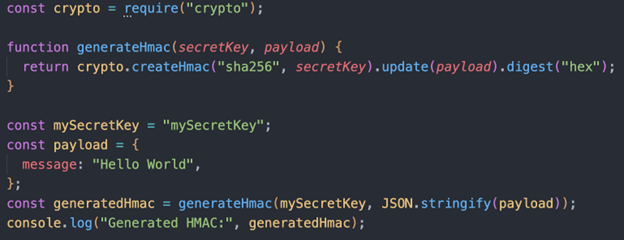
In this script, the generatedHmac variable will contain the HMAC signature for the given payload.
Next, we need to write a script that will validate a request using the HMAC signature. This script will also need two parameters: the payload of the request and the signature generated by the first script.
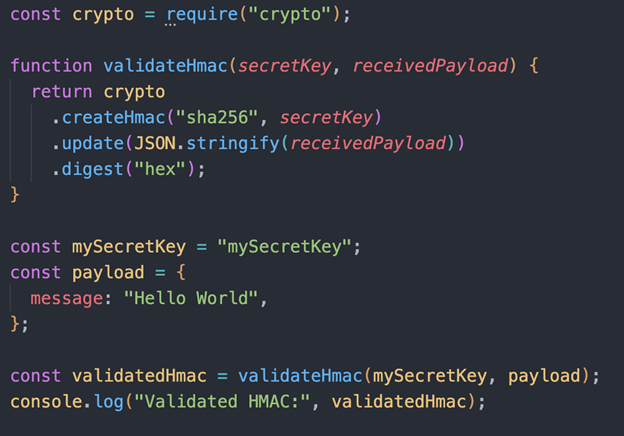
In this script, the secretKey variable will contain the HMAC signature for the given receivedPayload and key. If the validatedHmac variable matches the generatedHmac variable from the first script, then the request is considered valid. Otherwise, the request is considered invalid.
Although endpoint security is important, it's not foolproof. Therefore, it's important to use other methods to protect endpoints. Security is critical to your business so contact Sunrise Integration to discuss an audit or consultation on your API, webhooks or app project.